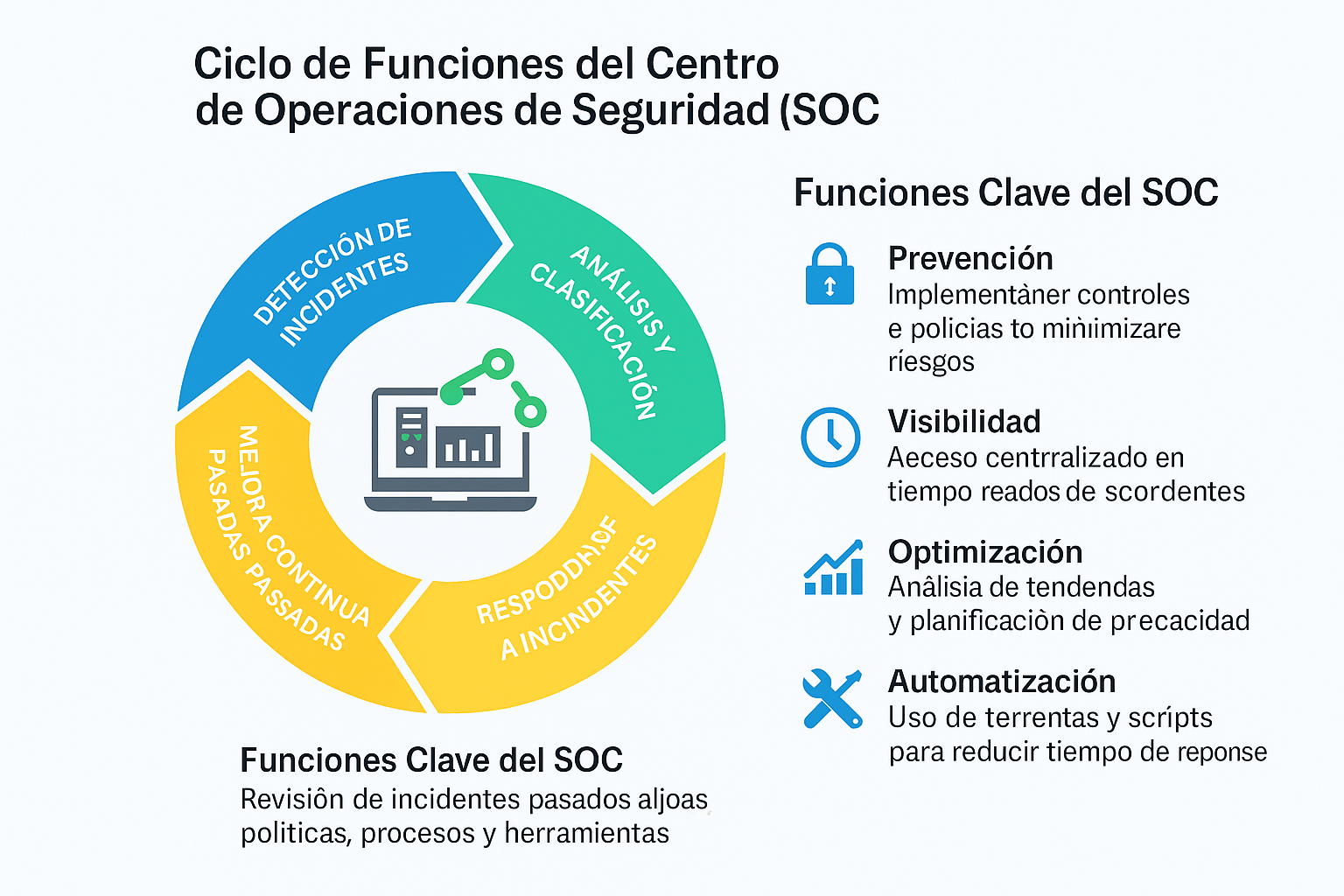
24/7 Continuous Monitoring and Detection
Continuous monitoring is the constant heartbeat of the SOC. Imagine having thousands of eyes watching every corner of your digital infrastructure, 24 hours a day, 7 days a week. This fundamental function allows for the real-time detection of anomalies before they become costly security breaches.
SOC analysts use advanced tools like SIEM (Security Information and Event Management) to correlate millions of events per second. Every failed login, every unusual data transfer, every connection from a suspicious location is instantly analyzed. This proactive monitoring reduces threat detection time from weeks to minutes, marking the difference between a thwarted attack attempt and a million-dollar data breach.
Key elements of continuous monitoring:
-
Real-time log analysis: Processing of logs from servers, applications, databases, and network devices to identify anomalous patterns.
-
Network traffic monitoring: Deep packet inspection (DPI) to detect malicious communications or data exfiltration.
-
Intelligent alerts: Prioritized notification systems that distinguish between false positives and real threats, avoiding alert fatigue.
-
Centralized dashboards: Unified visualization of the security status of the entire organization in real time.

Forensic Investigation and Analysis
When an anomaly is detected, the SOC transforms into a digital forensic laboratory. Analysts act as cyber detectives, reconstructing the chain of events to understand the what, how, when, and why of a security incident.
Forensic analysis goes beyond simply responding to an attack. It involves preserving digital evidence in a way that is admissible in legal proceedings, identifying the initial attack vector, determining the extent of the compromise, and, crucially, understanding the attacker's techniques to prevent similar future incidents.
This meticulous process includes:
-
Evidence preservation: Secure capture and storage of logs, volatile memory, disk images, and network traffic following the chain of custody.
-
Malware analysis: Decomposition of malicious code in sandbox environments to understand its behavior and capabilities.
-
Timeline reconstruction: Creation of a detailed timeline of the incident, from initial compromise to detection.
-
Identification of IOCs: Documentation of Indicators of Compromise to strengthen future defenses.
Incident Response
Speed is critical when facing an active threat. The SOC's incident response function is like a digital fire department: every second counts. A well-executed response plan can mean the difference between a minor incident and a business crisis.
The SOC follows a structured process based on the NIST incident response framework:
-
Preparation: Keeping playbooks updated, conducting drills, and ensuring tools are ready for immediate deployment.
-
Detection and Analysis: Confirming the nature of the incident, determining its severity and initial scope.
-
Containment: Isolating affected systems to prevent the lateral spread of the attack without alerting the attacker.
-
Eradication: Eliminating the threat at its root, closing attack vectors, and patching exploited vulnerabilities.
-
Recovery: Restoring systems to normal operation with intensified monitoring to detect persistence.
-
Lessons Learned: Documenting the incident and updating procedures to improve future response.
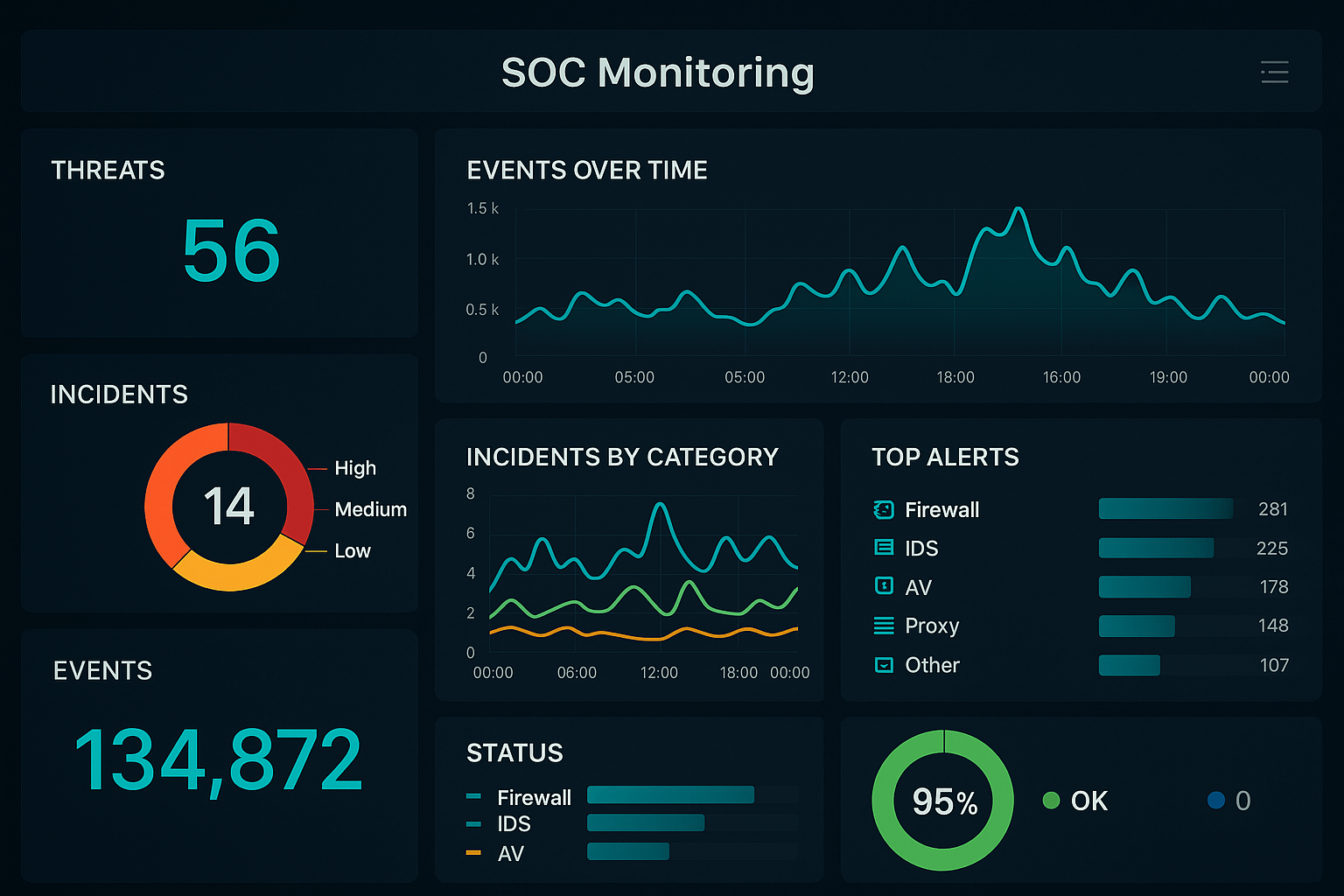
Vulnerability Management
Prevention is better than cure. Proactive vulnerability management is a critical function of the SOC that identifies and prioritizes weaknesses in the infrastructure before attackers can exploit them. It is a constant race against time, as new vulnerabilities are discovered every day.
The process is not limited to running automated scanners. It requires a holistic approach that considers the business context, the criticality of the assets, and the current threat landscape. The SOC works closely with IT teams to coordinate patches and mitigations without disrupting critical business operations.
Key components of vulnerability management:
-
Continuous scanning: Automated identification of vulnerabilities in systems, applications, and configurations.
-
Risk-based prioritization: Use of frameworks such as CVSS combined with threat intelligence to determine which vulnerabilities require immediate attention.
-
Patch management: Coordination with IT teams to apply critical updates while minimizing downtime.
-
Remediation validation: Verification that vulnerabilities have been effectively corrected without introducing new problems.
Threat Intelligence
Knowing your enemy is fundamental in cybersecurity. Threat intelligence transforms raw data about malicious actors, attack campaigns, and new techniques into actionable information that strengthens the organization's defenses.
The SOC does not operate in a vacuum. It constantly feeds on both commercial and open-source intelligence (OSINT) sources, participating in information sharing communities such as ISACs (Information Sharing and Analysis Centers). This contextualized intelligence allows for the anticipation of attacks specifically targeted at your industry or region.
Effective threat intelligence includes:
-
Tactical intelligence: Specific IOCs such as malicious IPs, malware hashes, and command and control domains.
-
Operational intelligence: TTPs (Tactics, Techniques, and Procedures) of specific threat groups.
-
Strategic intelligence: Emerging trends and long-term threats that inform security investment decisions.
-
Proactive threat hunting: Active search for latent threats based on hypotheses derived from intelligence.

Compliance and Reporting
In a world where privacy and security regulations are multiplying—GDPR, CCPA, HIPAA, SOX—the SOC plays a crucial role in demonstrating continuous compliance. It is not enough to be secure; you must be able to prove it with exhaustive and auditable documentation.
SOC reports range from real-time executive dashboards to detailed forensic reports for audits. Every action, every alert, every response is documented, creating an immutable record that satisfies both regulators and internal stakeholders.
Essential types of reports:
-
Executive reports: High-level KPI metrics on security posture, threat trends, and SOC ROI.
-
Compliance reports: Specific documentation aligned with regulatory frameworks and industry standards.
-
Incident reports: Detailed post-mortem analysis of significant incidents with recommendations for improvement.
-
Operational metrics: MTTD (Mean Time to Detection), MTTR (Mean Time to Response), and false positive rates.
Optimization and Maintenance of Security Tools
A SOC is only as effective as the tools it uses. Continuous optimization is not optional; it is essential to maintain effectiveness in the face of an ever-evolving threat landscape. This function ensures that each technological component operates at peak performance.
Maintenance goes beyond applying updates. It involves fine-tuning detection rules to reduce false positives, adjusting alert thresholds based on actual business behavior, and continuously evaluating new technologies that can strengthen the security posture. The SOC must constantly evolve or become obsolete.
Key optimization activities:
-
SIEM tuning: Continuous refinement of correlation rules and use cases to improve detection accuracy.
-
Process automation: Implementation of SOAR playbooks for automated responses to common threats.
-
Tool integration: Orchestration of multiple security solutions to create a cohesive ecosystem.
-
Evaluation of emerging technologies: Proof of concept with new solutions such as AI/ML for advanced detection.
The modern SOC is not a cost center, it is a business enabler. These seven functions work in harmony to create an impenetrable digital shield that allows your company to innovate with confidence, knowing that its most valuable assets are protected by experts 24 hours a day.