After understanding the immense value and return on investment that a Security Operations Center (SOC) can offer, the next logical step is to ask: Where do we start? The idea of creating a security operations center can seem like a monumental task, reserved only for the largest corporations. However, with careful planning and a phased approach, companies of any size can implement an effective SOC that protects their most valuable assets.
This practical guide breaks down the process into six manageable steps, from initial conception to operation and continuous improvement. Consider this article your roadmap, a SOC implementation plan designed to give you clarity and confidence at every stage of the journey.
Before You Start: The Key Strategic Decision (In-house vs. SOCaaS)
Before we dive into the steps, there is a fundamental decision that every company must make that will influence the entire process: whether to build an in-house SOC, hire a SOC as a Service (SOCaaS), or adopt a hybrid model.
- In-House SOC: Offers maximum control and customization. It requires a significant investment in personnel, technology, and processes. Ideal for large companies with very specific security requirements and the resources to maintain a 24/7 operation.
- SOC as a Service (SOCaaS): You outsource the operation to a specialized provider. It is faster to implement, often more economical, and provides immediate access to cutting-edge talent and technology. Ideal for SMEs and companies looking for a robust solution without a large initial investment.
- Hybrid Model: Combines an internal team (often for business context analysis and response) with a SOCaaS provider (for 24/7 monitoring and initial alert handling). It offers a balance between control and efficiency.
With this decision in mind, let's explore the steps to bring your SOC to life.
Step 1: Needs Assessment and Objective Definition
The biggest mistake when implementing a SOC is to start buying technology without a clear strategy. The first and most critical step is to understand what you need to protect and why.
Key Actions:
- Identify "Crown Jewels": What information or systems are most critical to the survival of your business? This could be customer data, intellectual property, production systems, e-commerce platforms, etc. Your SOC should be built around protecting these assets.
- Assess the Threat Landscape: What types of cyberattacks are most likely in your industry? Are you a target for ransomware, business email compromise (BEC), supply chain attacks, or data theft? Use threat intelligence reports to inform this assessment.
- Understand Compliance Requirements: Are you subject to regulations such as GDPR, HIPAA, PCI-DSS, or local data protection laws? The SOC will be essential to meet monitoring and breach notification requirements.
- Define Clear and Measurable Objectives: Don't just say "we want to improve security." Set concrete goals. For example:
- "Reduce the Mean Time to Detection (MTTD) of critical threats to less than 1 hour."
- "Achieve 95% monitoring coverage of critical assets within the first 6 months."
- "Ensure continuous compliance with PCI-DSS regulations through quarterly security reports."
The result of this step should be a SOC Mission Statement, a clear declaration that will guide all future decisions.
Step 2: Budget and Resource Planning
With the objectives defined, the next step is the financial reality. A SOC is an ongoing investment, not a one-time purchase. Your budget should cover three main areas:
- People: This is the most expensive and crucial component. It includes salaries, benefits, ongoing training, and certifications for SOC analysts and managers. If you opt for a SOCaaS, this cost translates into the provider's fee.
- Technology: This includes software licensing costs (SIEM, SOAR, EDR), hardware (if necessary), subscriptions to threat intelligence feeds, and annual maintenance.
- Processes and Facilities: This includes the development of playbooks, external consulting, and if it is an in-house SOC, the physical space, power, and connectivity.
Practical tip: When presenting the budget, link it directly to the risks identified in Step 1 and the potential ROI (as we saw in the previous article). Instead of saying "we need X for a SIEM," say "we need to invest X in a SIEM platform to mitigate the risk of a ransomware attack, which could cost us Y."
Step 3: Selecting the Right Technology
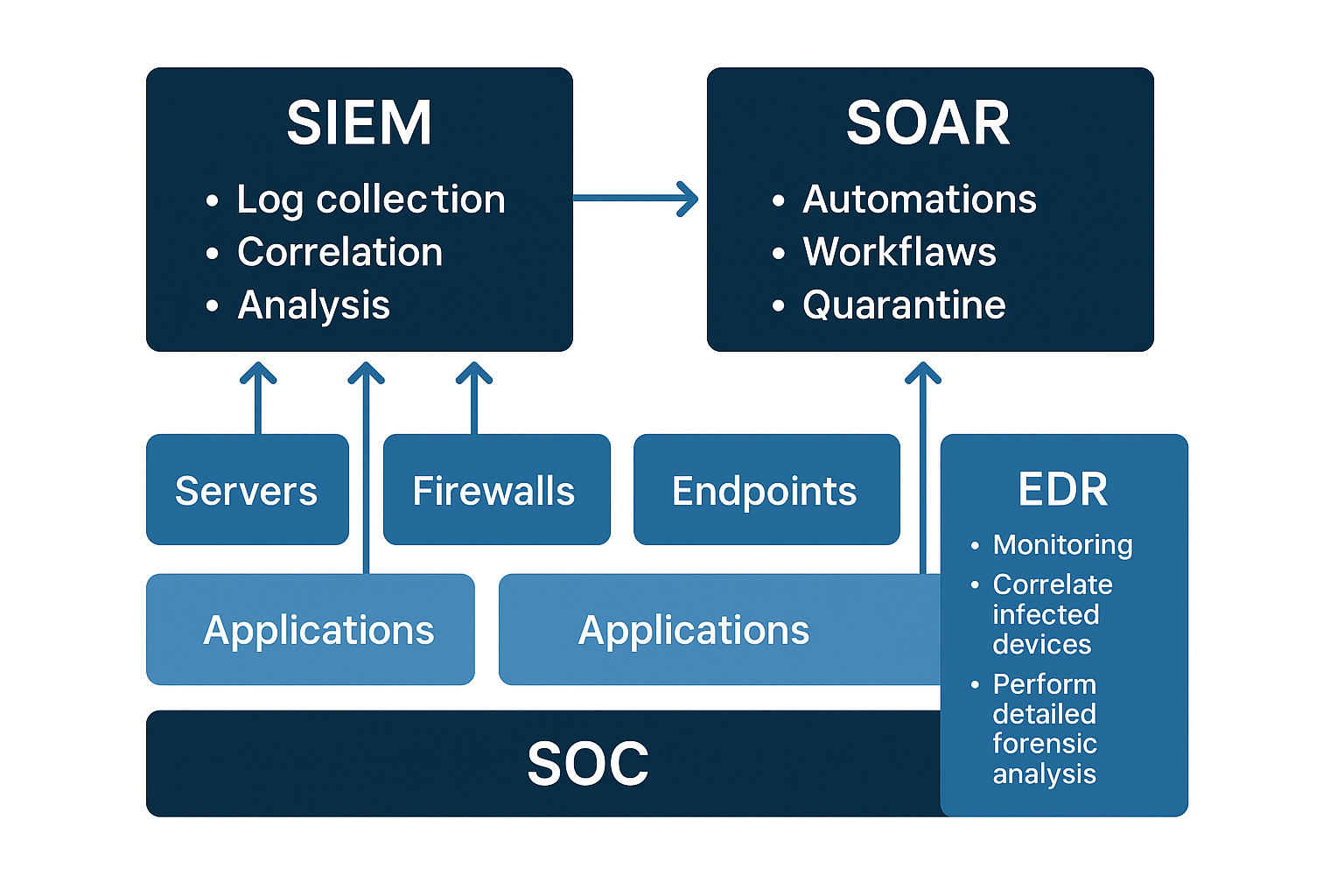
Technology is the backbone that allows your team to detect and respond to threats. The technology stack of a modern SOC is composed of several layers. The most fundamental tools for a SOC are:
- SIEM (Security Information and Event Management): It is the brain of the SOC. It aggregates, correlates, and analyzes log data from virtually all sources on your network (servers, firewalls, endpoints, applications). It looks for anomalous patterns and generates alerts when a potential threat is detected.
- SOAR (Security Orchestration, Automation, and Response): It is the muscular system. It automates repetitive tasks and orchestrates incident response workflows. For example, upon receiving an alert from the SIEM, a SOAR can automatically quarantine a device, block a malicious IP, or open a support ticket, freeing up analysts to focus on complex investigations.
- EDR (Endpoint Detection and Response): These are the guards on each device. EDR monitors activity on endpoints (laptops, servers) for malicious behavior that traditional antivirus might miss. It allows for the isolation of infected devices and detailed forensic analysis.
Other important technologies to consider include threat intelligence platforms (TIPs), network detection and response (NDR) systems, and vulnerability analysis tools. The key is to choose tools that integrate well with each other and align with your objectives and budget.
Step 4: Designing the Team Structure (Roles and Responsibilities)
People are the heart of the SOC. A well-defined SOC team structure ensures that alerts are handled efficiently and that there are no gaps in coverage. Typical roles include:
- Tier 1 Analyst (Triage Specialist): The first line of defense. They monitor incoming alerts, investigate them at a basic level to rule out false positives, and escalate legitimate incidents to Tier 2 analysts.
- Tier 2 Analyst (Incident Responder): They conduct in-depth investigations into escalated incidents. They analyze the scope of the attack, determine the root cause, and coordinate containment and eradication actions.
- Tier 3 Analyst (Threat Hunter): They are the experts and the most proactive. They do not wait for alerts to pop up. They actively search for hidden threats on the network ("threat hunting"), analyze advanced malware, and stay up-to-date on the latest attacker tactics.
- SOC Manager: The strategic leader. They oversee daily operations, manage the team, define success metrics (KPIs), communicate with management, and ensure the SOC is aligned with business objectives.
For smaller companies, it is common for a single person to perform multiple roles or for these roles to be covered by a SOCaaS provider. The important thing is that all these responsibilities are clearly assigned.
Step 5: Developing Processes and Playbooks
A SOC without defined processes is just a group of talented people reacting to chaos. Processes and playbooks (response guides) are the script that ensures a consistent, rapid, and effective response to any incident.
A playbook is a set of step-by-step instructions that an analyst should follow when faced with a specific type of threat. You should develop playbooks for the highest-risk scenarios identified in Step 1.
Example of a Playbook Structure for a Ransomware Alert:
- Detection: How was the alert generated? (SIEM, EDR, etc.)
- Validation: Confirm that it is not a false positive (are any files being encrypted?).
- Containment: Immediately isolate the affected device from the network (EDR/SOAR action).
- Analysis: Identify the ransomware strain and its entry vector (was it through a phishing email, a vulnerability?).
- Eradication: Remove the malware and close the entry point.
- Recovery: Restore data from clean backups.
- Post-incident: Document the incident, analyze lessons learned, and improve defenses.
Having these processes documented reduces stress, minimizes human error, and dramatically speeds up response time.

Step 6: Defining Metrics (KPIs) and SLAs
What doesn't get measured, doesn't get improved. To justify the ongoing investment in the SOC and ensure its effectiveness, you need to define key performance indicators (KPIs) and Service Level Agreements (SLAs).
Essential KPIs for a SOC:
- Mean Time to Detection (MTTD): The average time it takes for the SOC to detect a threat from the time it occurs.
- Mean Time to Response (MTTR): The average time it takes for the SOC to neutralize a threat once detected. (The goal is to reduce both to a minimum).
- Number of Critical Incidents Handled: Shows the workload and direct value in preventing disasters.
- False Positive Rate: An indicator of the efficiency and tuning of your tools.
- Visibility Coverage: The percentage of critical assets that are being monitored by the SOC.
SLAs are performance promises, especially important if you work with a SOCaaS or if you report to management. For example: "For high-priority incidents, the initial response time will be less than 15 minutes."
Estimated Implementation Timeline
Although every company is unique, a phased timeline can be as follows:
- Phase 1: Planning and Design (1-3 months): Includes Steps 1 and 2. Needs assessment, objective definition, budget planning, and model selection (in-house vs. SOCaaS).
- Phase 2: Technology Acquisition and Implementation (2-4 months): Includes Step 3. Negotiation with vendors, installation, and initial configuration of the SIEM, EDR, etc.
- Phase 3: Hiring and Process Development (2-4 months): Includes Steps 4 and 5. Hiring the team (if in-house) and developing the initial playbooks.
- Phase 4: Go-live and Optimization (Ongoing): Includes Step 6. The SOC becomes operational. KPIs begin to be measured, and a cycle of continuous improvement is initiated, refining rules, processes, and tools.
Total estimate for a basic operational SOC: 6 to 12 months.
Conclusion: A Journey of Continuous Improvement
Implementing a SOC is a strategic journey, not a project with an end date. It is the creation of a living, breathing capability that evolves with your business and the threat landscape. By following these steps and using our SOC checklist, you will transform a daunting goal into a series of achievable accomplishments. The result will not only be a set of tools and analysts but a true culture of cyber resilience that will protect your company today and in the future.
Value-Added Element: Your Downloadable Checklist
To help you navigate this complex process, we have created a complete SOC implementation checklist in an easy-to-follow format. You can access it directly from HERE.