Definition and Basic Concepts: What is a SOC?
A SOC (Security Operations Center) is the brain and heart of an organization's cybersecurity strategy. Think of it as an air traffic control tower, but instead of airplanes, it monitors, detects, and responds to digital threats in real time, 24/7.
Its main mission is to protect the company's digital assets—such as customer data, intellectual property, and critical infrastructure—from an increasingly sophisticated landscape of cyberattacks. It achieves this through a centralized approach that unifies people, processes, and technology to continuously manage security.
In formal terms, a SOC is defined as:
"A centralized facility where a team of security experts monitors, analyzes, and protects an organization's technological infrastructure, using a set of defined tools and processes to prevent, detect, and respond to cybersecurity incidents."

Importance in Today's Cybersecurity
In 2025, the question is no longer *if* a company will suffer a cyberattack, but *when*. The proliferation of IoT devices, remote work, and cloud migration have expanded the attack surface, making proactive defense indispensable. A SOC is crucial for several reasons:
-
Rapid Detection and Response: A SOC dramatically reduces the time between detecting a threat and neutralizing it (known as MTTR or Mean Time to Response), minimizing financial and operational impact.
-
Unified Visibility: It centralizes the monitoring of the entire infrastructure (networks, servers, endpoints, cloud applications), allowing the identification of anomalous patterns that would otherwise go unnoticed.
-
Threat Intelligence: It stays updated on the latest tactics, techniques, and procedures (TTPs) of cybercriminals, allowing the company to anticipate potential attacks.
-
Regulatory Compliance: It helps comply with strict data protection regulations such as GDPR, HIPAA, or the Fintech Law, by providing constant security audits and reports.
Investing in a SOC is not an expense, it is an investment in business continuity and customer trust.
Types of SOC: In-house, Outsourced, and Hybrid
There is no one-size-fits-all solution for all companies. The choice of SOC model depends on the organization's size, budget, security maturity level, and internal resources.
1. In-house SOC
The company builds, manages, and operates its own Security Operations Center with directly hired personnel.
Ideal for: Large corporations with high-value assets and mature IT teams that require full control over their security operations.
2. Outsourced SOC (Managed or SOC-as-a-Service)
A managed security service provider (MSSP) is hired to offer 24/7 monitoring and response. It is a subscription model that provides access to experts and cutting-edge technology without the initial investment.
Ideal for: Small and medium-sized enterprises (SMEs) or companies that want a quick and cost-effective implementation without the burden of hiring and retaining specialized talent.
3. Hybrid SOC
It combines the best of both worlds. The company's internal team collaborates closely with an external SOC provider. Typically, the internal team handles the business context and final response, while the provider handles 24/7 monitoring and initial analysis.
Ideal for: Companies that have a security team but need to expand their monitoring capacity and access specialized knowledge.
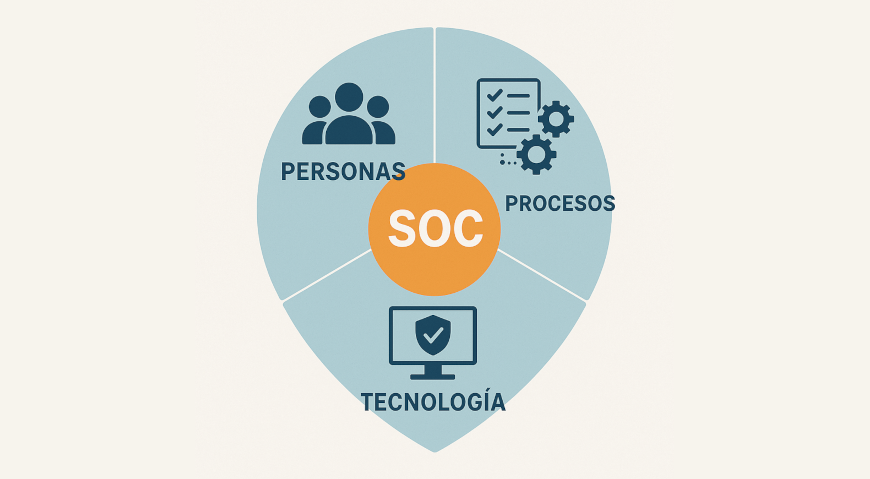
Main Components of a SOC
An effective SOC relies on three fundamental pillars that work in perfect sync:
1. People (The Human Team)
It is the most critical component. It includes specialized roles such as security analysts (Tier 1, 2, and 3), security engineers, threat hunters, and a SOC director. Their expertise is vital for interpreting data and making sound decisions.
2. Processes (The Playbooks)
These are the standardized operating procedures that guide the team. They clearly define how to handle each type of alert or incident: from initial detection and classification to threat eradication and system recovery. These "playbooks" ensure a consistent and effective response.
3. Technology (The Cybersecurity Arsenal)
This is the set of tools that the team uses to have visibility and response capability. Key technology includes:
-
SIEM (Security Information and Event Management): The heart of the SOC. It aggregates and correlates logs from multiple sources to detect suspicious activities.
-
SOAR (Security Orchestration, Automation, and Response): Automates repetitive incident response tasks, allowing the human team to focus on complex threats.
-
EDR/XDR (Endpoint/Extended Detection and Response): Provides deep visibility and response capability on endpoints (laptops, servers) and across the entire infrastructure.
-
Threat Intelligence Platforms (TIP): Feed the SOC with updated information on new threats, vulnerabilities, and malicious actors.
The synergy between these people, processes, and technologies is what makes a SOC the indispensable digital fortress for any business in the modern era.